cfgssl
实战:利用cfgssl自签证书-2023.1.5(测试成功)
目录
[toc]
实验环境
bash
linux机器实验软件
链接:https://pan.baidu.com/s/13nee2xk30Y8-z9TdpuZOuA?pwd=9zzp
提取码:9zzp
2023.1.5-cfgssl软件包
1、安装cfgssl工具
- 将cfssl工具安装包和脚本上传到服务器:
bash
[root@k8s-master1 ~]#ls -lh cfssl.tar.gz
-rw-r--r-- 1 root root 5.6M Nov 25 2019 cfssl.tar.gz
-rw-r--r-- 1 root root 1005 Mar 26 2021 certs.sh
[root@k8s-master1 ~]#tar tvf cfssl.tar.gz
-rwxr-xr-x root/root 10376657 2019-11-25 06:36 cfssl
-rwxr-xr-x root/root 6595195 2019-11-25 06:36 cfssl-certinfo
-rwxr-xr-x root/root 2277873 2019-11-25 06:36 cfssljson
[root@k8s-master1 ~]#tar xf cfssl.tar.gz -C /usr/bin/- 验证:
bash
[root@k8s-master1 ~]#cfssl --help
Usage:
Available commands:
bundle
certinfo
ocspsign
selfsign
scan
print-defaults
sign
gencert
ocspdump
version
genkey
gencrl
ocsprefresh
info
serve
ocspserve
revoke
Top-level flags:
-allow_verification_with_non_compliant_keys
Allow a SignatureVerifier to use keys which are technically non-compliant with RFC6962.
-loglevel int
Log level (0 = DEBUG, 5 = FATAL) (default 1)2、生成证书
- 创建测试目录:
bash
[root@k8s-master1 ~]#mkdir https
[root@k8s-master1 ~]#cd https/- 将证书生成脚本移动到刚才创建的目录
bash
[root@k8s-master1 ~]#mv certs.sh https/
[root@k8s-master1 ~]#ls https/
certs.sh
[root@k8s-master1 ~]#cd https/
[root@k8s-master1 https]#cat certs.sh
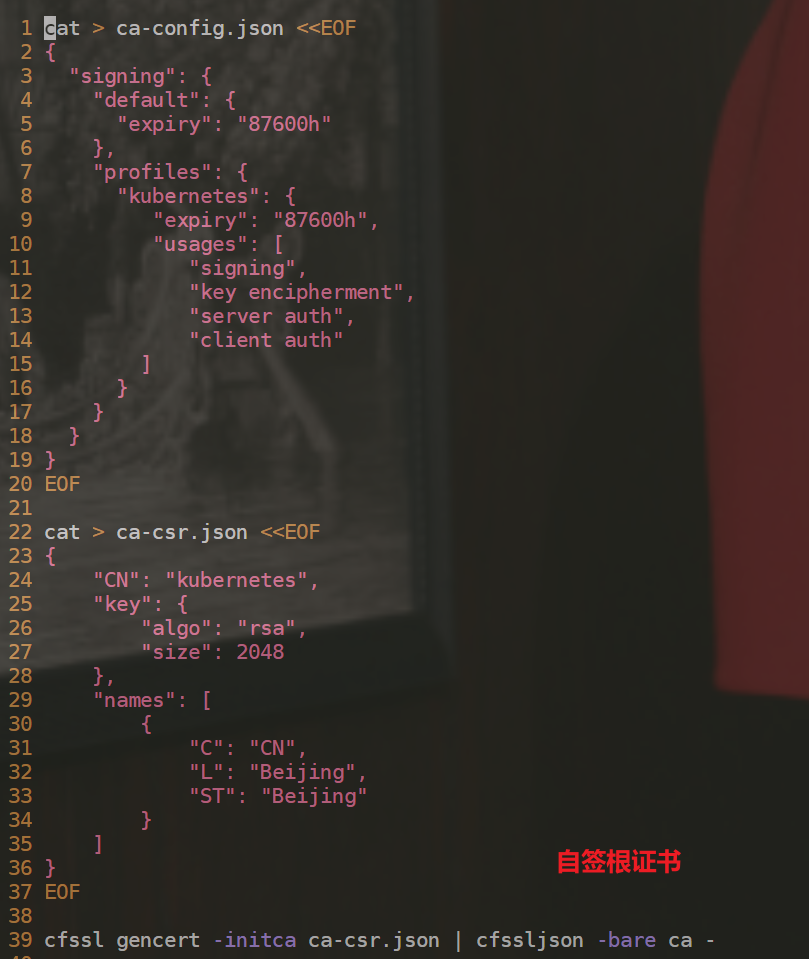
cat > ca-config.json <<EOF
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"kubernetes": {
"expiry": "87600h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
EOF
cat > ca-csr.json <<EOF
{
"CN": "kubernetes",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "Beijing",
"ST": "Beijing"
}
]
}
EOF
cfssl gencert -initca ca-csr.json | cfssljson -bare ca -
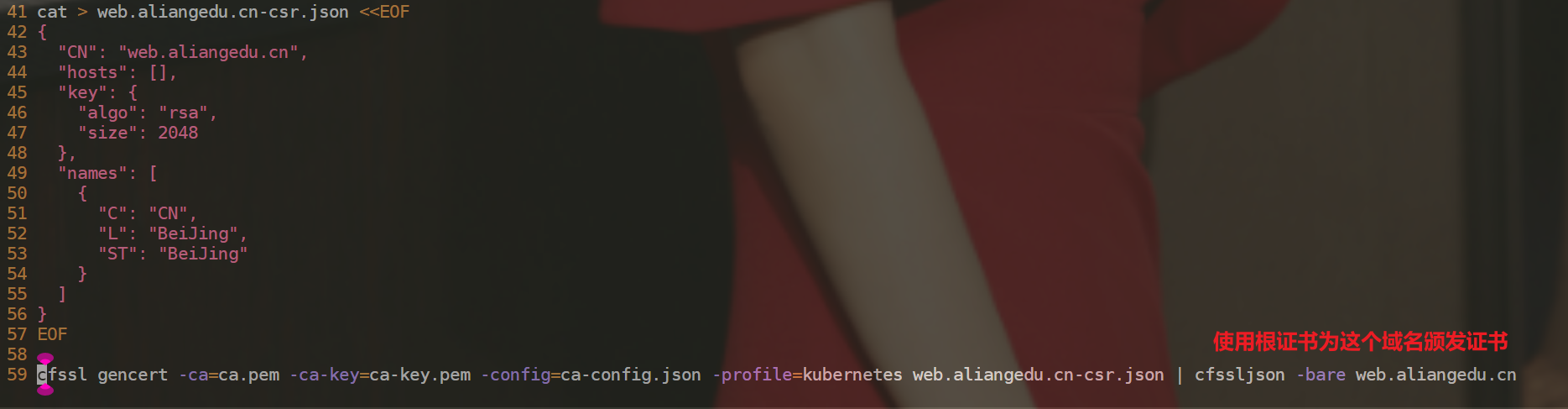
cat > web.aliangedu.cn-csr.json <<EOF
{
"CN": "web.aliangedu.cn",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "BeiJing",
"ST": "BeiJing"
}
]
}
EOF
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes web.aliangedu.cn-csr.json | cfssljson -bare web.aliangedu.cn备注:
- 执行脚本,生成证书:
bash
[root@k8s-master1 https]#sh certs.sh
2022/11/27 09:38:30 [INFO] generating a new CA key and certificate from CSR
2022/11/27 09:38:30 [INFO] generate received request
2022/11/27 09:38:30 [INFO] received CSR
2022/11/27 09:38:30 [INFO] generating key: rsa-2048
2022/11/27 09:38:30 [INFO] encoded CSR
2022/11/27 09:38:30 [INFO] signed certificate with serial number 42920572197673510025121729381310395494775886689
2022/11/27 09:38:30 [INFO] generate received request
2022/11/27 09:38:30 [INFO] received CSR
2022/11/27 09:38:30 [INFO] generating key: rsa-2048
2022/11/27 09:38:30 [INFO] encoded CSR
2022/11/27 09:38:30 [INFO] signed certificate with serial number 265650157446309871110524021899155707215940024732
2022/11/27 09:38:30 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").
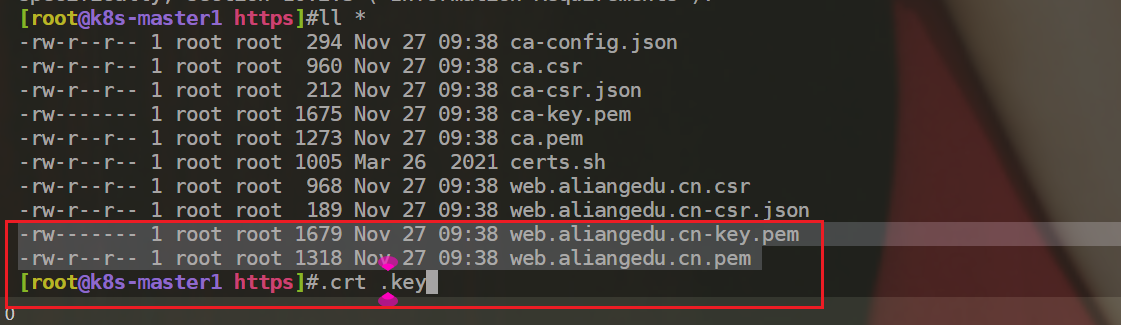
[root@k8s-master1 https]#ll *
-rw-r--r-- 1 root root 294 Nov 27 09:38 ca-config.json
-rw-r--r-- 1 root root 960 Nov 27 09:38 ca.csr
-rw-r--r-- 1 root root 212 Nov 27 09:38 ca-csr.json
-rw------- 1 root root 1675 Nov 27 09:38 ca-key.pem
-rw-r--r-- 1 root root 1273 Nov 27 09:38 ca.pem
-rw-r--r-- 1 root root 1005 Mar 26 2021 certs.sh
-rw-r--r-- 1 root root 968 Nov 27 09:38 web.aliangedu.cn.csr
-rw-r--r-- 1 root root 189 Nov 27 09:38 web.aliangedu.cn-csr.json
-rw------- 1 root root 1679 Nov 27 09:38 web.aliangedu.cn-key.pem #数字证书私钥
-rw-r--r-- 1 root root 1318 Nov 27 09:38 web.aliangedu.cn.pem #数字证书
[root@k8s-master1 https]#- 注意:这个后缀不一样,
.crt,.key。
参考文章
参考1:
此处为语雀内容卡片,点击链接查看:https://www.yuque.com/xyy-onlyone/zo9184/schvzu
参考2:
具体路径:
bash
3、RBAC
实战2:只能访问某个 namespace 的普通用户-2023.2.6(测试成功)(cfgssl)
关于我
我的博客主旨:
- 排版美观,语言精炼;
- 文档即手册,步骤明细,拒绝埋坑,提供源码;
- 本人实战文档都是亲测成功的,各位小伙伴在实际操作过程中如有什么疑问,可随时联系本人帮您解决问题,让我们一起进步!
🍀 微信二维码
x2675263825 (舍得), qq:2675263825。

🍀 微信公众号
《云原生架构师实战》

🍀 语雀
https://www.yuque.com/xyy-onlyone
https://www.yuque.com/xyy-onlyone/exkgza?# 《语雀博客》
🍀 博客
www.onlyyou520.com
🍀 csdn
https://blog.csdn.net/weixin_39246554?spm=1010.2135.3001.5421
🍀 知乎
https://www.zhihu.com/people/foryouone
最后
好了,关于本次就到这里了,感谢大家阅读,最后祝大家生活快乐,每天都过的有意义哦,我们下期见!

